Honghong will provide you with any support you need!
Our professional Honghong team will be the first to respond and provide you with the best service to solve all your problems.

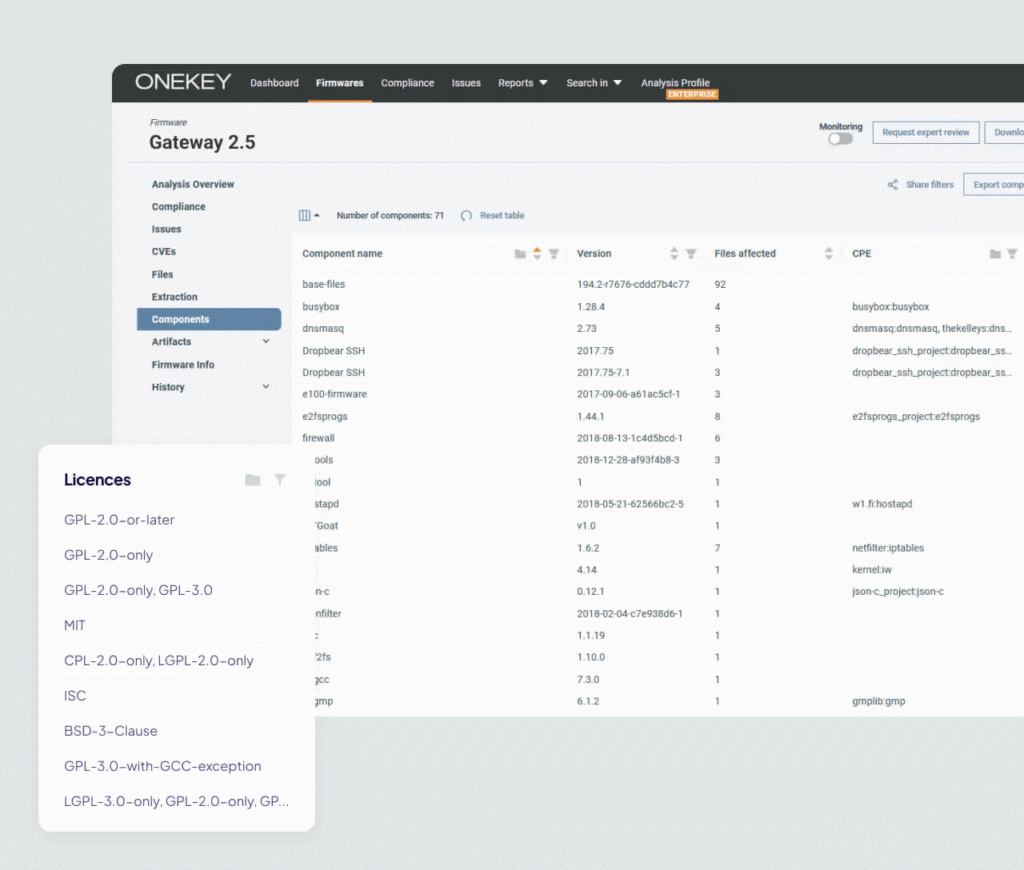
Your centralized solution: Full lifecycle monitoring with support for SBOM validation, vulnerability detection and prioritization, zero-day vulnerability detection, and regulatory and compliance. Covers the entire software development lifecycle (SDLC), helping you build more secure products that comply with industry standards, intelligently defend against attacks, and automate security closures.

A user-friendly interface for development teams, Product Safety Incident Response Teams (PSIRTs) and product managers. Click-and-go operation saves time and reduces costs.
From product design to go-to-market maintenance, all network security and compliance needs are fully supported on the same platform.
It's not just about tools, it's about utilizing the knowledge of our global research team and experts. The developers of the platform are also available to assist you with consulting services.
End-to-end platform helps simplify security processes and ease compliance requirements
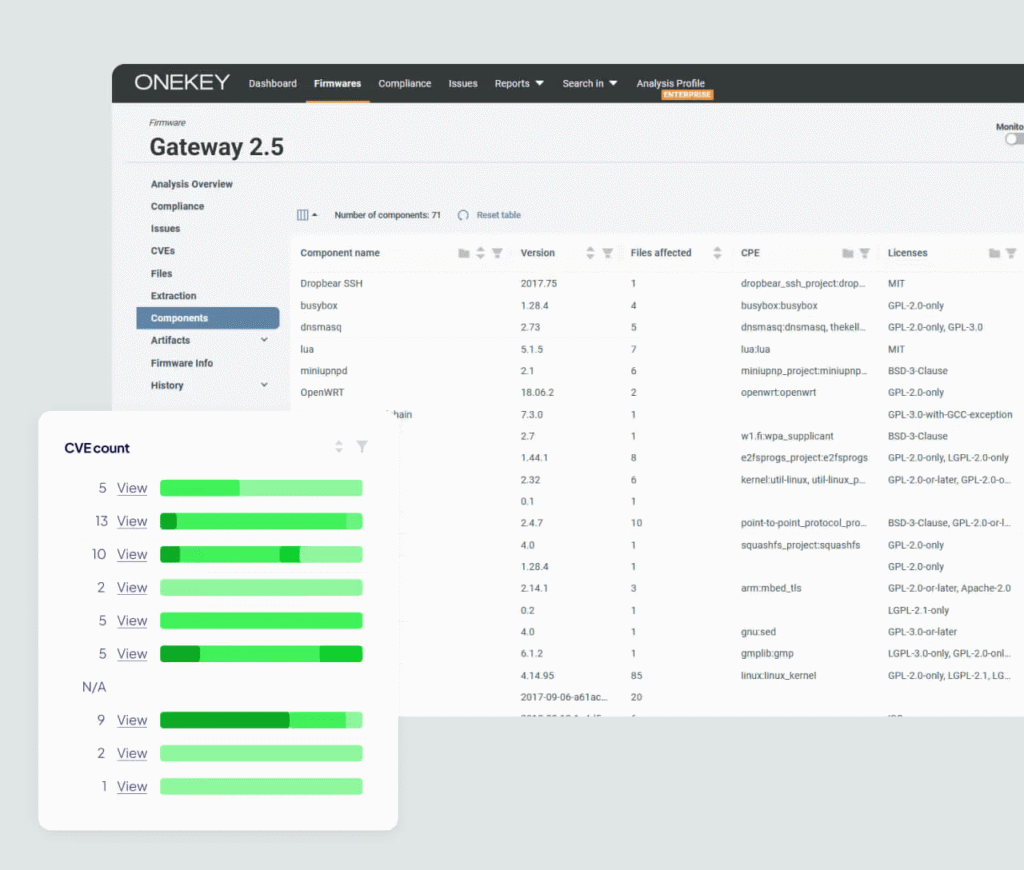
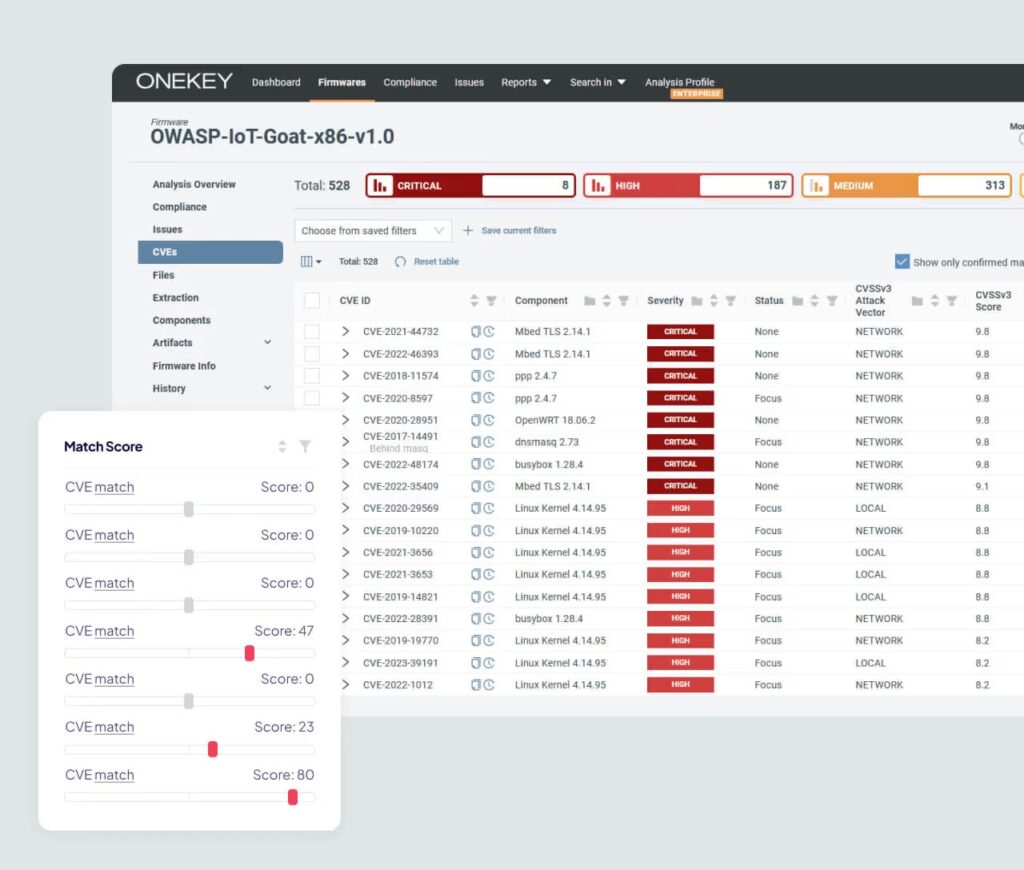
Focus on Critical Vulnerabilities
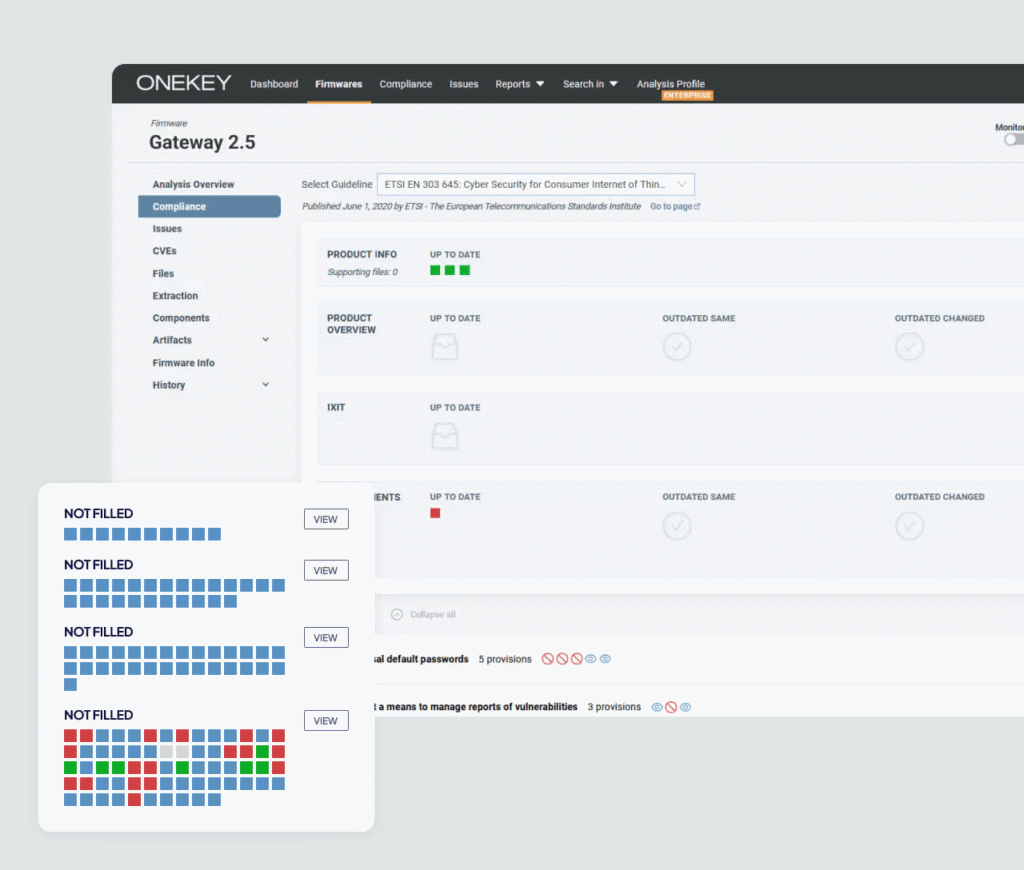
Easily meets compliance requirements
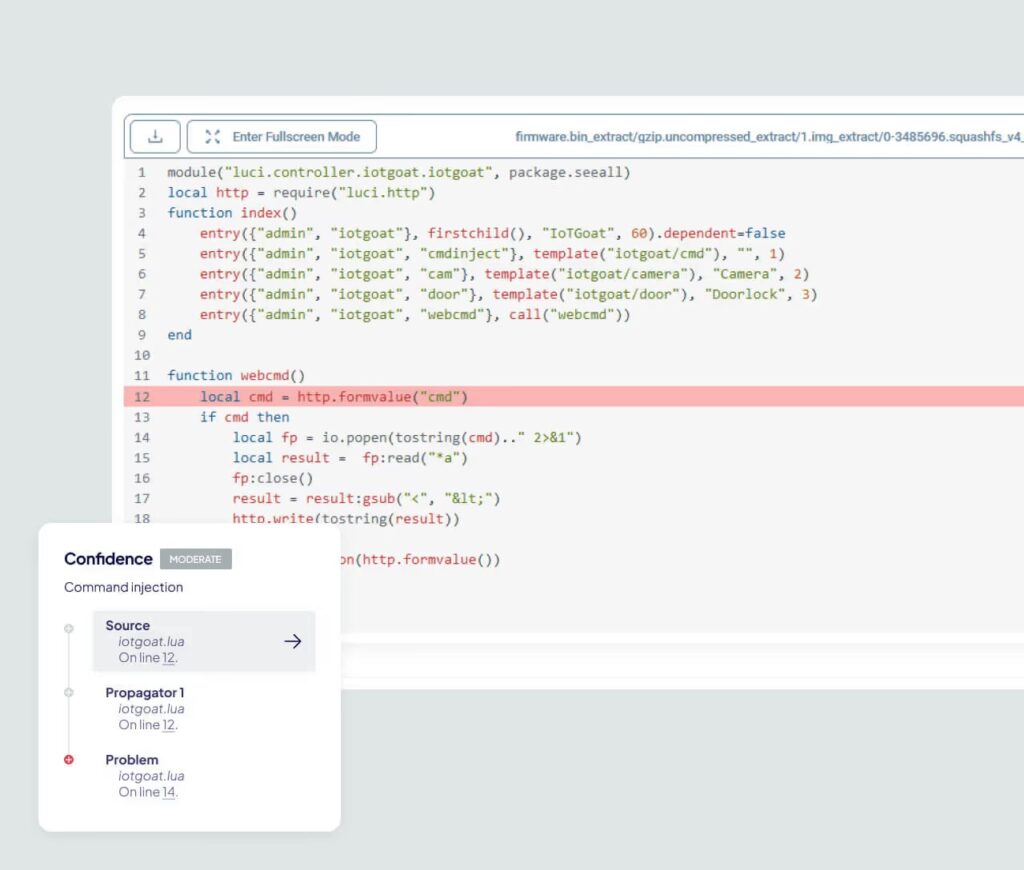
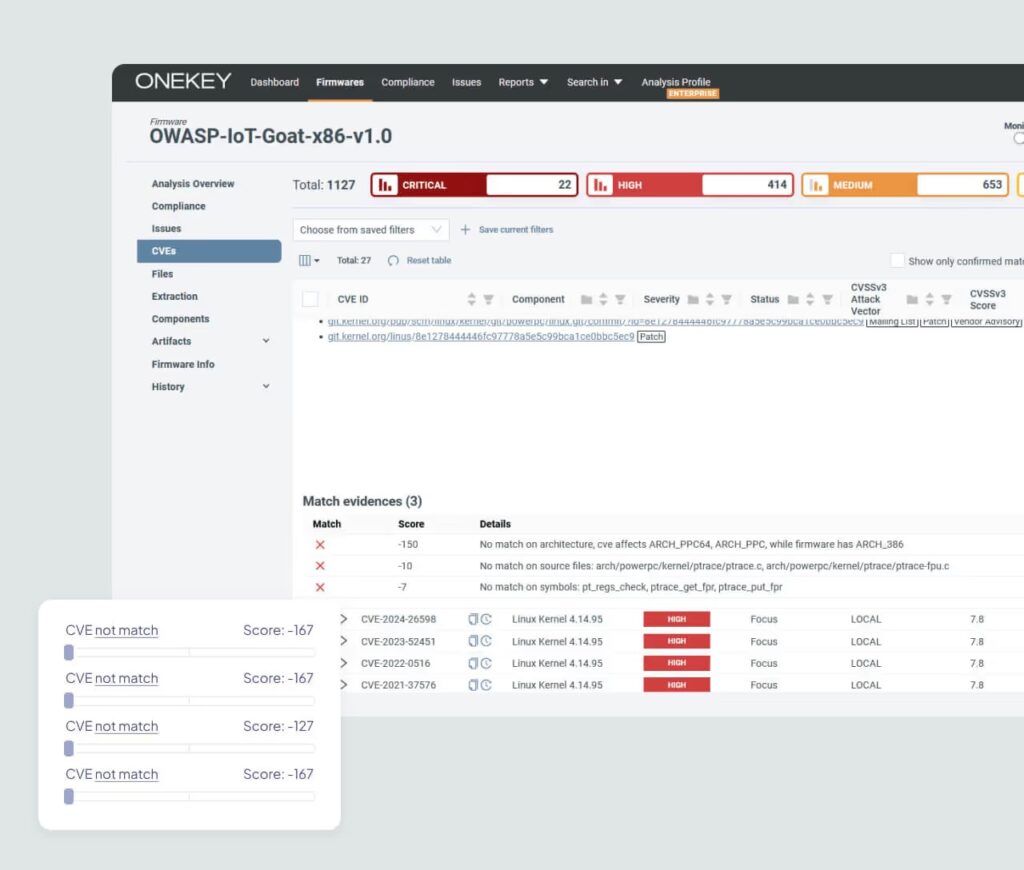
Real-time Risk Scanning
Avoiding Legal Risks
Flexible Threat Modeling
Manufacturing
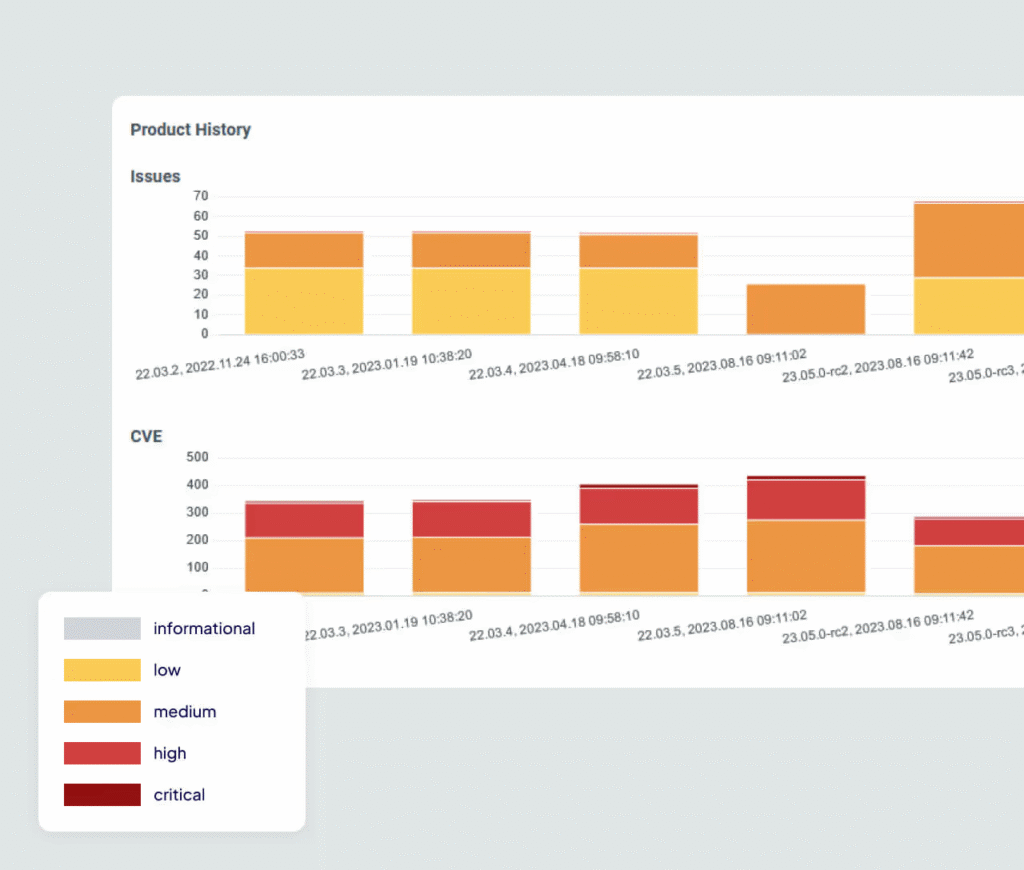
Discover new ways to keep IoT/IIoT/OT networks secure and compliant. Receive real-time alerts from the firmware's digital feeds and continuously monitor connected devices at scale. Effectively meet regulatory standards and prevent costly downtime and security risks.
Reducing Operational Risks through a Transparent Supply Chain
automobile industry
ONEKEY provides advanced standalone vulnerability detection and analysis. Seamless integration with ETAS CycurRISK enables holistic analysis from development to deployment, complying with ISO/SAE 21434, ISO 26262/IEC 61508 and other relevant standards.
Secure and Reduce Risks in the Software Supply Chain
Medical
ONEKEY detects vulnerabilities at all stages of development through SBOM and provides digital monitoring to support your FDA and EU MDR compliance efforts, ensuring that your medical devices are safe and fit for market.
Avoid monopoly and loss of key products

Support for SSO enabled by all OpenID Connect compatible identity providers

Integration of automated quality control in CI/CD scheduling tools

Automatically detects threats and creates work orders with SIEM tools

Use dashboards and KPI tools to share data with stakeholders

Create tasks in work order systems, project management and productivity tools

Uploading and querying analytics through DevOps tools
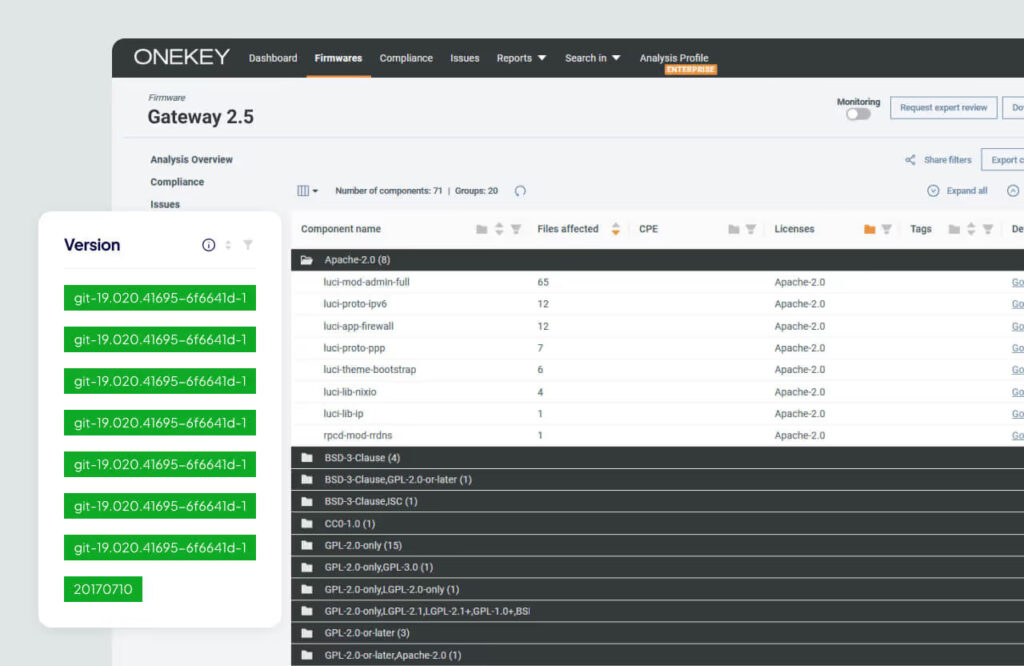
With the ONEKEY platform, you get comprehensive security protection from development to market. Our solutions provide continuous monitoring, automated vulnerability detection and regular updates to block emerging threats, ensuring that your products maintain a high level of security at every stage.
With a unified platform like ONEKEY, you can dramatically optimize your safety and compliance processes. That means fewer people working, lower operating costs, and a clearer overview of the security status of your products. You'll be able to respond to security threats faster and ensure that your products always meet the latest security standards.
ONEKEY integrates seamlessly with GitLab, Jenkins, Jira, and other development tools.By embedding automated security checks into existing development processes, you can identify and fix vulnerabilities early in the development process without additional burden, ensuring that the development process remains efficient and secure at the same time.
Automation technology dramatically reduces manual labor, saves time and lowers error rates.ONEKEY allows your team to focus on what really matters to your business by automating vulnerability assessments, compliance checks and threat detection.This not only improves the overall security level of products and systems, but also helps you to respond to various security risks more quickly and effectively.
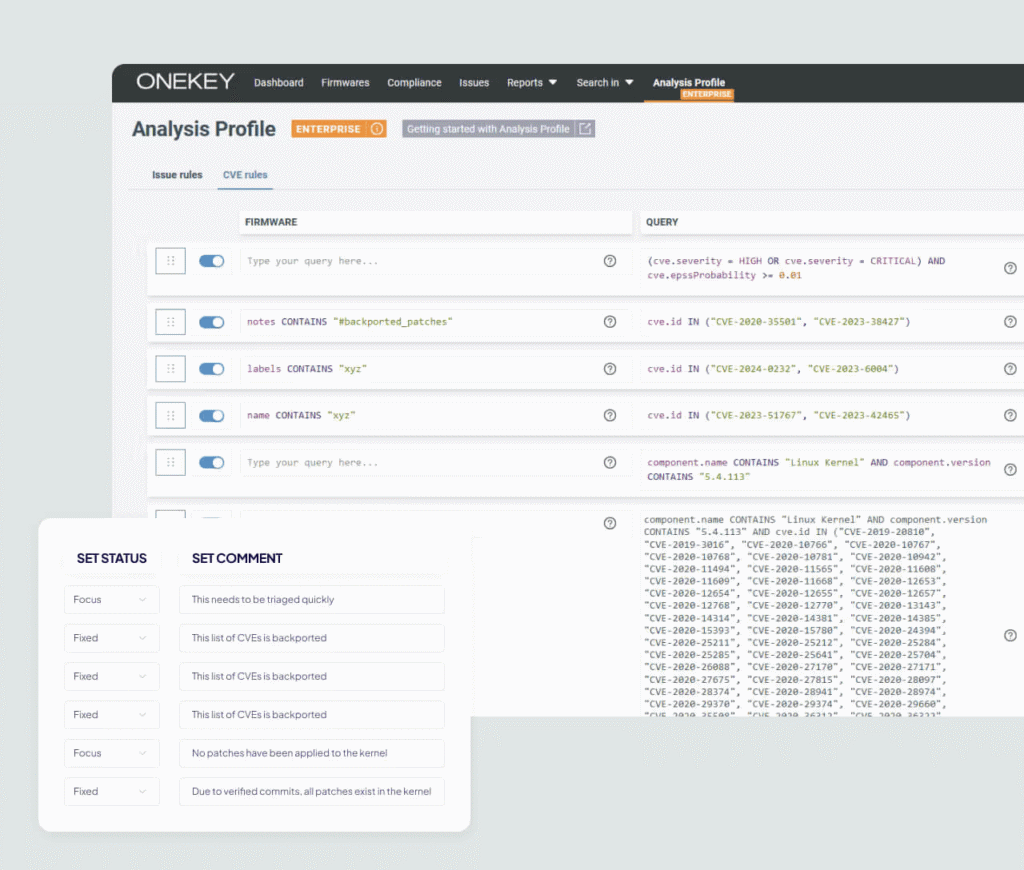
ONEKEY's exclusive Compliance Wizard™ feature keeps track of the latest developments in relevant network security standards.It helps you to quickly recognize the latest regulatory requirements and to comply with them with minimal adjustment costs.Make your compliance management process simpler and more efficient with automated change alerts and reminders.
Continuously build, comply, defend and repeat with the advanced Compliance Wizard™.
ONEKEY is usA key tool for application security and compliance management. Continuous, automated security assessments not only increase the transparency of our clients' projects, but also ensure compliance with EU CRA regulations. In addition, ONEKEY's real-time insights and feedback allow us to provide clear, actionable product and network security recommendations to our customers.
![]()
Timon Bergman | Application Solutions Manager
ONEKEY's automated binary software simplifies snap one's product security process, reducing 70% manual operations while increasing the vulnerability detection rate by 3 times. This dramatically improves management efficiency while increasing product transparency and credibility. The excellent support provided by the expert team also makes the system connection smooth.![]() Connie Gray | Senior Director, Engineering Networks and Product Safety
Connie Gray | Senior Director, Engineering Networks and Product Safety
Working with ONEKEY has been an eye-opening experience.Their security expertise exceeded expectations.![]() Nigel Hanson | AppSec+ Hardware Security Specialist
Nigel Hanson | AppSec+ Hardware Security Specialist
We want to use the industry's best tools and solutions for ongoing firmware monitoring and vulnerability assessment, and ONEKEY's automated software analytics effectively help us provide our customers with industry-leading quality of service for product lifecycle security monitoring while ensuring efficiency.
![]()
Joël Conus | Vice President, IoT R&D and Services
ONEKEY's ability to automate the detection of critical vulnerabilities in embedded devices allows us to more efficiently dedicate manual testing resources to business logic validation, increasing overall security testing efficiency by 40%.
![]()
Wolfgang Baumgartner | Head of Global Security Consulting
We use ONEKEY to detect potential risks before all software releases go live, and analyze and fix any issues immediately after release. The security of new features and interfaces is fully guaranteed.
![]()
Giulio Grazzi | IoT Senior Security Advisor
Conduct an initial needs assessment with an information security expert to understand your actual pain points.
Experience a personalized presentation of the platform's features based on your business context.
Receive a customized solution that includes the details of your requirements to help you get your project off the ground quickly.
Our professional Honghong team will be the first to respond and provide you with the best service to solve all your problems.
Address: 3F, No. 99, Jingye 1st Road, Zhongshan District, Taipei City, Taiwan (Da Wan Technology Center Building)
3rd Floor., Dawan Technology Center Building, No. 99 Jingye 1st Road, Zhongshan District, Taipei City, Taiwan
©2025.hongtronics. All Rights Reserved.