preamble
As the EU's Cyber Resilience Act (CRA) officially enters its final days, the pressure on organizations to comply with product security and regulations is increasing. According to the "Internet of Things and OT Network Security Report 2025" survey, currently only 32% businesses truly understand the specific requirements of the CRA.In addition, the proportion of businesses that have initiated full compliance measures is even higher.Only 14%This shows that the majority of enterprises still have a lack of awareness and implementation of CRA.
ONEKEY is releasing a report based on the 300 industrial and manufacturing related companiesThe sample was used to reveal the real status of each enterprise's CRA compliance progress through verifiable data. From the results, we can see that there is still a gap between "knowing the regulations" and "taking action" in most enterprises. As CRA enters the final stage of implementation, enterprises need to accelerate their pace to fill in the gaps in their understanding of regulations, security governance processes and compliance implementation, so as to avoid future impacts on product exports, supply chain cooperation and market compliance.
i. background to the introduction of the cra statute
As the world accelerates its digital transformation, technologies such as the Internet of Things (IoT) and Industrial Control Systems (ICS) have been deeply integrated into manufacturing, transportation, energy, and healthcare industries. However, the security risks associated with digitization are also rising rapidly. According to statistics from the German Federal Office for Information Security (BSI) and the Criminal Police Bureau (BKA).Cybercrime in Germany is estimated to cost €178.6 billion in 2024The increase of €30.4 billion over the previous year shows that the overall security situation is still deteriorating.
Against this backdrop, the EU officially launched the Cyber Resilience Act (CRA), the first EU law to coverEntire ICT/IoT Product AreaThe legislation is a mandatory information security regulation to fill the gap in the regulation of the safety of digital products in the past. The law willDirectly applicable to all EU member statesIt is a very important part of the process, and it is enforced in a mandatory manner.
CRA Important Timeline:
September 2026: First wave of compliance obligations in force
2027: All requirements fully implemented
At that time, any IoT device, device machine, software or hardware system that does not meet the CRA requirements will beNot allowed to enter or sell in the EU marketThe company may be unable to meet the requirements of the law. Businesses that fail to meet the requirements of the law may face Up to €15 million 或 Global Revenue 2.5% The higher the fine, the more likely it is, the more likely it is that the board of directors, officers or responsible persons will be held personally liable.Although some enterprises have already begun to make preparations for CRA compliance, the survey shows that most of them are still far from fully complying with the CRA requirements. In the face of the countdown to CRA compliance, industries need to accelerate their efforts to complete their information security governance and process setups in order to avoid falling into an unfavorable position in the EU market competition.
Core Obligations and Corporate Responsibilities under the CRA Regulations
The Cyberfirmware Act (CRA) has had an impact on theManufacturers, Suppliers & DistributorsA set of clear and mandatory safety requirements has been proposed, the core spirit of which is:Safety must start at the product design stage and continue throughout the product life cycle.。This extends to the entire lifecycle of the product, and organizations must ensure that unauthorized access, data integrity and confidentiality are maintained throughout the life of the product, and that core functionality is not disrupted by a security incident.
The CRA also emphasizes the timeliness of vulnerability reporting. Manufacturers are required to report to ENISA (European Network Security Agency) and national CSIRTs within 24 hours of discovering a vulnerability that has been exploited by an attacker or an incident of sufficient significance to affect the security of a product. This is considered one of the most challenging obligations of the CRA, as companies need to be able to monitor and react quickly.
After a product is released to the market, vendors remain responsible for maintaining long-term security, including continuously releasing security updates, patching known vulnerabilities, and providing complete and transparent product documentation. This documentation must include a SBOM (Software Bill of Materials) that allows users and authorities to trace the origin and risk of all software components in the product. For the manufacturing industry, where most products have lifecycles spanning several years, this requirement means that the responsibility for security maintenance is formally institutionalized and puts some pressure on companies to make progress toward CRA compliance.
Overall, CRA is not only a regulatory requirement, but also redefines the role of "network security" in product design, maintenance and after-sales service. Enterprises that fail to start preparing for CRA early will face higher compliance costs and market risks in the future.
III. Status of Compliance with the CRA Regulations
From the latest "Internet of Things and OT Network Security Report 2025", we can see that most enterprises' understanding of CRA is still far from adequate to support complete compliance actions. Survey results show that only about one-third (32%) of enterprises have a clear understanding of the core requirements of the CRA; another 30% of enterprises have studied the regulation but remain at the conceptual level; and even nearly 30% (27%) are completely unclear about the content and impact of the CRA. This gap in knowledge has become the primary obstacle for enterprises to move towards compliance.
Lack of Awareness: Significant Gaps Remain in CRA Requirements for Businesses
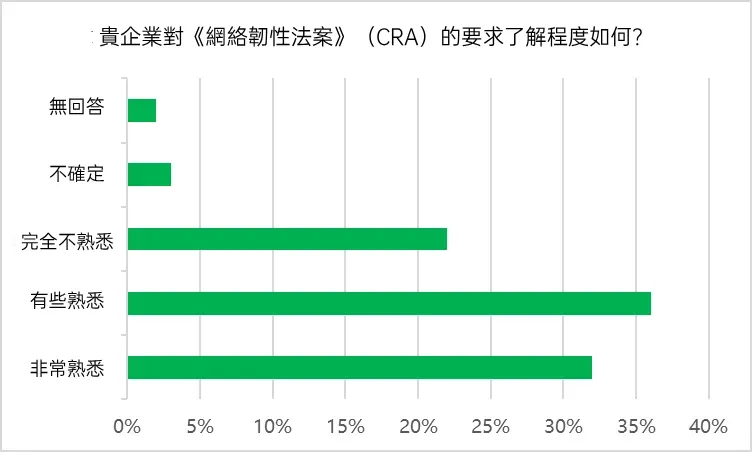
The data from the Internet of Things and OT Network Security Report 2025 shows a clear lack of understanding of CRA-related knowledge among organizations. Only about one-third (32%) of the respondents indicated that they fully grasp the specific requirements of the CRA; another 36% have not yet truly understood the content of the specification despite having conducted a preliminary survey; and the remaining 27% confessed that they are completely unfamiliar with the CRA, and they do not even understand whether they will be affected.
Due to the lack of awareness, the number of enterprises that have really started to establish a CRA compliance mechanism is even more limited. At present, only 28% enterprises have set up cross-departmental working groups to coordinate product, R&D, legal and security teams to prepare for CRA compliance; and another 14% enterprises have set up a dedicated team to take charge of the whole process of compliance implementation. However, as many as one-third (32%) of the organizations have yet to establish any kind of CRA working group, indicating that most organizations are still lagging behind in their CRA compliance preparations.
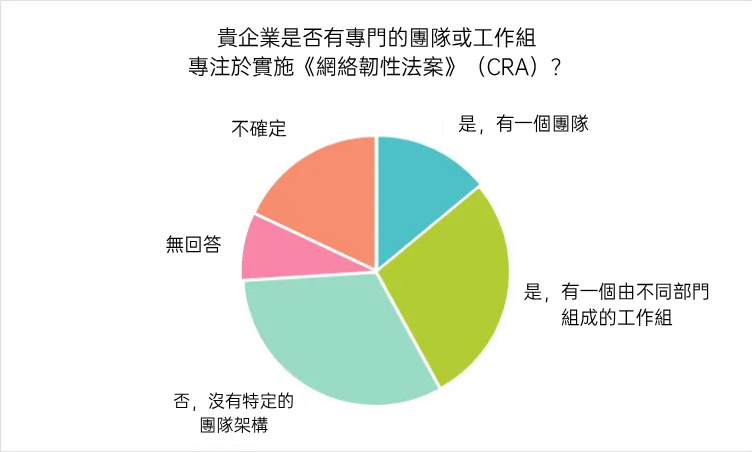
Overall, there are obvious gaps in enterprises' understanding of CRA, as well as large gaps in their internal governance and organizational readiness. Without accelerated investment in the future, it is highly likely that they will be subjected to compliance pressure and even market risks after the regulation officially comes into effect.
Slow progress of implementation
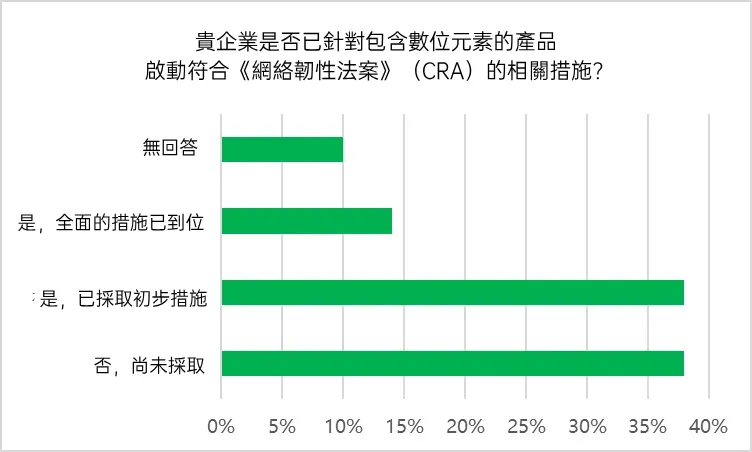
From the survey results, it is clear that companies are lagging behind in the actual implementation of the CRA. Only 14% enterprises have initiated complete and comprehensive compliance measures to ensure that their IoT devices, machines and systems comply with the CRA requirements. Another 38% have only made preliminary preparations, such as internal discussions or initial assessments, but have not yet established institutionalized processes. More than half of the remaining companies have yet to take any CRA-related action, indicating that the industry as a whole is still in the early stages of facing the new EU regulation.
In terms of policy formulation, the situation is not very optimistic either. Only 15% enterprises have formulated compliance policies specifically for CRA, which is obviously on the low side. In contrast, 34% respondents believe that the existing information security policies are sufficient to cover CRA requirements, but there may be a gap between this perception and the actual requirements. In addition, there are still 21% enterprises that have not included CRA in their compliance framework at all, showing that they still lack full understanding of the importance and impact of the new regulation.
Overall, the progress of the CRA has lagged far behind the mandatory entry into force of the regulation. As companies face the risk of not being able to import their products into the EU market, or even high penalties if they continue to delay, now is the critical time to accelerate the strengthening of internal policies and compliance processes.
Nearly 30% Companies Struggle with SBOM: Transparency Requirements the Biggest Bottleneck
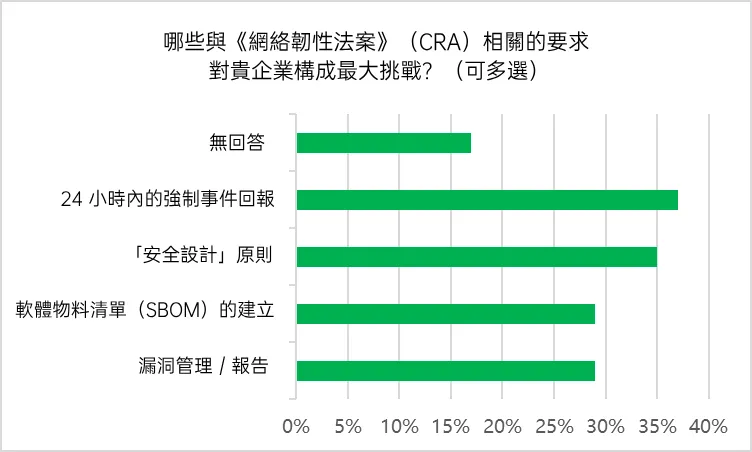
Among the CRA's various obligations, organizations generally found the requirement to report security incidents within 24 hours to be the most challenging, followed by the need to implement the principles of "secure by design" and "pre-designed security" at the product design stage. In particular, 29% of the respondents pointed out that the most difficult part of the requirement is to "establish a software bill of materials (SBOM) and continuously monitor all software components and vulnerabilities in the future.
SBOM (Software Bill of Materials) can be regarded as the software version of the "Bill of Parts," covering libraries, package dependencies, and version information, which is an important foundation for enhancing software transparency and shortening vulnerability analysis time. Without an SBOM, it is difficult for organizations to quickly determine whether a security vulnerability will affect their products, which can delay the time to fix it. Therefore, establishing a standardized, sustainably maintained SBOM process is a critical step in improving product resilience and strengthening security governance, especially in production environments where large numbers of devices are deployed and updates are frequent.
It is worth noting that although 44% enterprises have started to build SBOMs, only 12% have actually completed building SBOMs for all their products; another 32% have built SBOMs for only some of their products; 25% have not yet started, and another 25% of respondents even think that they will not be affected or have not yet understood the scope of the responsibility of SBOMs in the CRA. There are still 25% who have not yet started and another 25% who even think they will not be affected or do not fully understand the scope of SBOM responsibilities in the CRA.
Overall, SBOM has become a major sticking point for enterprises on the road to CRA compliance, showing that there is still a significant gap between organizations in terms of software asset transparency and vulnerability management processes. Starting SBOM construction now is still a critical time for enterprises to catch up with the CRA schedule.
Fuzzy division of safety responsibilities and unclear roles within enterprises
When asked who is responsible for ensuring compliance with the CRA, the majority of responses were highly dispersed, indicating that there is still a lack of consensus on where responsibility lies within the organization.
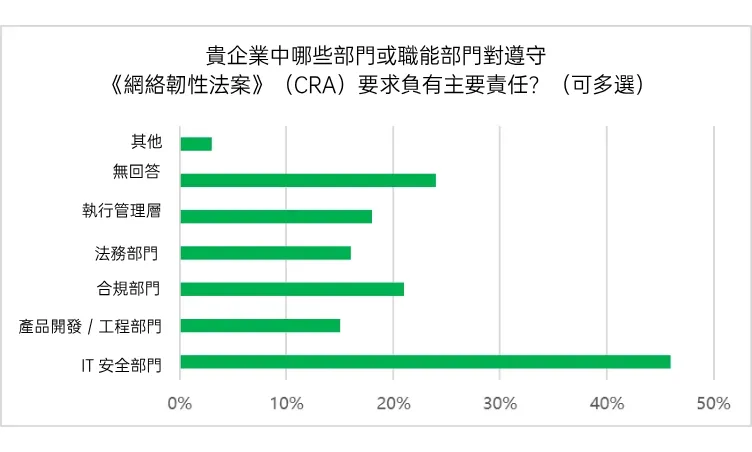
According to the survey results, about 46% enterprises have their CRA compliance work led by the IT security department, 21% are coordinated by the compliance department, 16% by the legal department, another 18% are directly led by the top management, and even 15% have assigned the CRA compliance responsibility to the product R&D team. On the whole, most enterprises have adopted a multi-departmental approach, but the boundaries of responsibility have not been clearly defined.
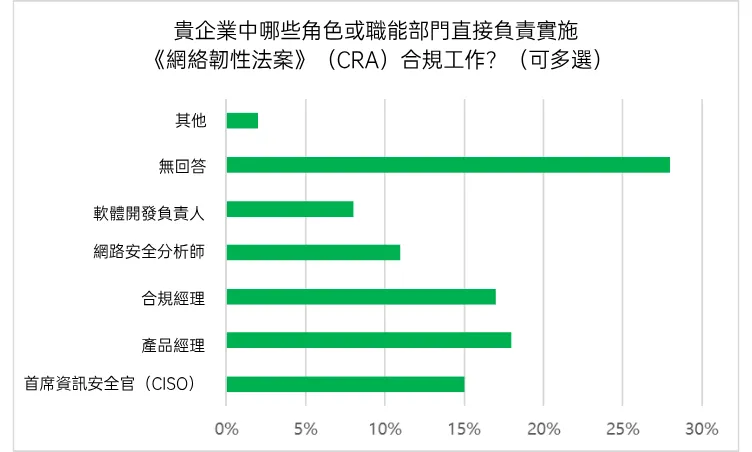
A similar fragmentation of roles was observed for specific responsible parties: 18% assigned CRA compliance responsibilities to product managers; 17% to compliance managers; 15% to CISOs (Chief Information Security Officers); 11% to security analysts; and 8% to software development executives. This distribution of roles reflects the potential for duplication, gaps, or cross-management between departments and functions in an organization's CRA compliance preparation.
In other words, although enterprises have begun to realize the pressure brought by CRA and try to establish internal responsibility chains, most of them have not yet formed a clear, consistent, and implementable configuration of authority and responsibility, and if they do not make timely adjustments in the future, it may cause bottlenecks in internal collaboration and compliance implementation after CRA is formally launched.
Suggestions for Action: How to Complete Key Layouts in the Final Countdown Stage of the CRA
As CRA is about to go into effect, enterprises are no longer facing a single compliance issue, but a "security fitness test" across the product lifecycle. From design, development, supply chain to vulnerability management, every step of the process needs to lead to secure design, establish a sustainable SBOM, and enhance product transparency and risk traceability. The earlier an organization starts to prepare, the more effective it will be in reducing future compliance costs.
Compliance is not only an obligation, but also an opportunity to rebuild competitiveness. When a product is sufficiently resilient, it is easier for a company to gain the trust of the international market and enter the EU supply chain. On the contrary, if they fail to meet the deadline, they not only face the risk of exiting the market, but also the long-term impact of fines and damage to goodwill.
CRA is a watershed in the global supply chain security requirements. Enterprises that are able to plan ahead, implement vulnerability management, maintain SBOM, and strengthen cross-departmental collaboration will be the first to cross the compliance threshold and turn compliance into a core advantage of market trust and brand competitiveness.
 If you would like to learn more about CRA regulatory requirements, the SBOM build process, or assess your organization's current compliance maturity, we can help you navigate through the ONEKEY Automated Security Analytics PlatformThe new system is designed to enhance product firmware and shorten compliance timelines to keep your IoT/OT system competitive in the face of the new EU regime in 2026!
If you would like to learn more about CRA regulatory requirements, the SBOM build process, or assess your organization's current compliance maturity, we can help you navigate through the ONEKEY Automated Security Analytics PlatformThe new system is designed to enhance product firmware and shorten compliance timelines to keep your IoT/OT system competitive in the face of the new EU regime in 2026!


